Security Operations Center (SOC) tools drive robust threat detection, monitoring, and response, forming the nerve center of organizational cybersecurity in 2026.
Security Information and Event Management (SIEM) platforms like Splunk and LogRhythm centralize logs, deliver advanced analytics, and accelerate incident investigations.
Endpoint Detection and Response (EDR) solutions such as CrowdStrike Falcon provide real-time endpoint protection with forensic depth.
Extended Detection and Response (XDR) platforms extend visibility across endpoints, networks, cloud, and users for unified threat hunting.
Threat Intelligence Platforms (TIPs) deliver actionable insights on emerging risks, while Intrusion Detection and Prevention Systems (IDS/IPS) monitor and block malicious traffic proactively.
Governance, Risk, and Compliance (GRC) tools automate workflows for regulatory adherence, and Next-Generation Firewalls (NGFW) enforce deep packet inspection to secure network perimeters.
These integrated capabilities empower SOC teams to outpace sophisticated attacks.
How Does SOC Tools Use?
SOC tools are used to centralize, automate, and enhance the security operations of an organization by identifying, monitoring, managing, and mitigating security risks in real time. Here’s how SOC tools are typically used:
- Continuous Monitoring and Detection: SOC tools collect, correlate, and analyze data from various sources such as endpoints, networks, cloud environments, and applications to detect suspicious activity and potential threats as they occur.
- Automated Incident Management: These tools automate the detection, triage, and response to security incidents, reducing manual workload and accelerating remediation. They can assign severity levels, trigger predefined responses (like isolating devices or blocking malicious IPs), and streamline incident workflows.
- Threat Intelligence and Analytics: SOC tools leverage advanced analytics, machine learning, and threat intelligence feeds to identify anomalies, detect insider threats, and prioritize high-risk alerts for investigation.
- Compliance and Reporting: They provide comprehensive logging, reporting, and audit capabilities to ensure regulatory compliance (such as PCI DSS, HIPAA, GDPR) and to support post-incident analysis and continuous improvement.
What are Important of SOC Tools?
SOC tools are critically important for modern organizations because they enable effective and efficient management of cybersecurity risks and threats. Here are the key reasons why SOC tools are essential:
- Enhanced Threat Detection and Response: SOC tools rapidly identify, analyze, and respond to security incidents, minimizing potential damage and operational downtime by automating threat detection and streamlining incident management.
- Continuous Monitoring: They provide round-the-clock surveillance of networks, endpoints, cloud environments, and applications, ensuring that threats are detected and addressed in real time, regardless of when they occur.
- Improved Visibility and Situational Awareness: SOC tools aggregate and correlate data from multiple sources, giving security teams a comprehensive view of the organization’s security posture and enabling better decision-making.
- Automation and Efficiency: By automating repetitive tasks and centralizing security data, SOC tools enhance the productivity of security teams, allowing them to focus on high-priority threats and investigations.
- Compliance and Reporting: SOC tools support regulatory compliance by providing detailed audit trails, real-time monitoring, and customizable reporting for standards such as PCI DSS, HIPAA, and GDPR.
- Reduced Cybersecurity Costs: Effective use of SOC tools can lower overall cybersecurity expenses by preventing breaches, reducing incident response times, and minimizing duplication of effort across teams.
What is Benefits of SOC Tools?
SOC tools provide numerous benefits that strengthen an organization’s cybersecurity posture and operational resilience. Key benefits include:
- Continuous Monitoring: SOC tools enable 24/7 surveillance of networks, endpoints, and cloud environments, ensuring threats are detected and addressed as they emerge.
- Immediate Threat Detection and Response: These tools quickly identify, analyze, and respond to security incidents, minimizing potential damage and operational downtime by automating threat detection and streamlining incident management.
- Enhanced Visibility and Situational Awareness: SOC tools aggregate and correlate data from multiple sources, giving security teams a comprehensive view of the organization’s security posture and enabling better decision-making.
- Automation and Efficiency: By automating repetitive tasks and centralizing security data, SOC tools boost productivity, allowing teams to focus on high-priority threats and investigations.
- Cost Savings: Effective use of SOC tools reduces overall cybersecurity expenses by preventing breaches, reducing incident response times, and minimizing duplication of effort across teams.
- Improved Compliance: SOC tools support regulatory compliance by providing detailed audit trails, real-time monitoring, and customizable reporting for standards such as PCI DSS, HIPAA, and GDPR.
10 SOC Tools in 2026
- SolarWinds Security Event Manager: Real-time event log monitoring and automated threat response.
- Splunk: Powerful data analytics platform for security information and event management.
- TrendMicro XDR: Comprehensive extended detection and response with advanced threat correlation.
- Trellix Platform: Integrated security operations with advanced threat detection and response.
- ArcSight: Scalable SIEM solution with real-time threat detection and compliance reporting.
- Exabeam: User and entity behavior analytics for efficient threat detection.
- Rapid7 Insight Platform: Unified cloud-based security management and vulnerability assessment.
- CrowdStrike Falcon: Endpoint protection with real-time threat intelligence and response.
- Log360: Comprehensive log management and network security monitoring.
- McAfee ESM (Enterprise Security Manager): Centralized security information management with advanced analytics.
10 Best SOC Tools List And Their Features
| Tool | Log Collection/Correlation | Threat Detection | Incident Response | Compliance Reporting | User/Entity Behavior Analytics | Automation/SOAR | Integration with 3rd Party Tools | Cloud Support |
|---|---|---|---|---|---|---|---|---|
| 1. SolarWinds Security Event Manager | Yes | Yes | Yes | Yes | Limited | Limited | Yes | Limited |
| 2. Splunk | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes |
| 3. TrendMicro XDR | Yes | Yes | Yes | Limited | Yes | Yes | Yes | Yes |
| 4. Trellix Platform | Yes | Yes | Yes | Limited | Yes | Yes | Yes | Yes |
| 10. ArcSight | Yes | Yes | Yes | Yes | Limited | Yes | Yes | Limited |
| 5. Exabeam | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes |
| 6. Rapid7 Insight Platform | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes |
| 7. CrowdStrike Falcon | Limited | Yes | Yes | Limited | Yes | Yes | Yes | Yes |
| 8. Log360 | Yes | Yes | Yes | Yes | Limited | Limited | Yes | Limited |
| 9. McAfee ESM | Yes | Yes | Yes | Yes | Limited | Limited | Yes | Limited |
1. SolarWinds Security Event Manager
.webp.jpeg)
SolarWinds Security Event Manager (SEM) is one of the most competitive entry-level SIEM tools today. The SEM includes all of the key capabilities you’d anticipate from an SIEM system, including sophisticated log management and reporting.
SolarWind’s thorough real-time incident response makes it an excellent tool for companies wishing to actively manage their network infrastructure against future attacks by leveraging Windows event logs.
SolarWinds Security Event Manager is an on-premises solution that can also communicate with cloud systems. This solution can monitor many websites and cloud storage from a central location on one of the servers.
One of SEM’s main features is its comprehensive and user-friendly interface design. The dashboard’s simplicity facilitates the user’s comprehension of any irregularities.
As a plus, the organization provides help around the clock, so you may call them for assistance if you encounter a problem.
Main Features:
- Real-time event correlation and automated threat response for rapid incident detection and mitigation.
- Centralized log collection, parsing, normalization, and management from diverse sources.
- Comprehensive compliance reporting with customizable templates for industry standards like PCI DSS, HIPAA, and SOX.
- Advanced search, forensic tools, and user activity monitoring for in-depth security investigations.
| What is Good ? | What Could Be Better ? |
|---|---|
| Enterprise-focused SIEM with many integrations | Compared to competitors, offers minimal security analytics. |
| Log filtering without query language training | May not scale for huge companies. |
| Dozens of themes let administrators customize SEM programs with minimum setup. | |
| A historical analysis tool for outliers and unexpected network activity. |
2. Splunk
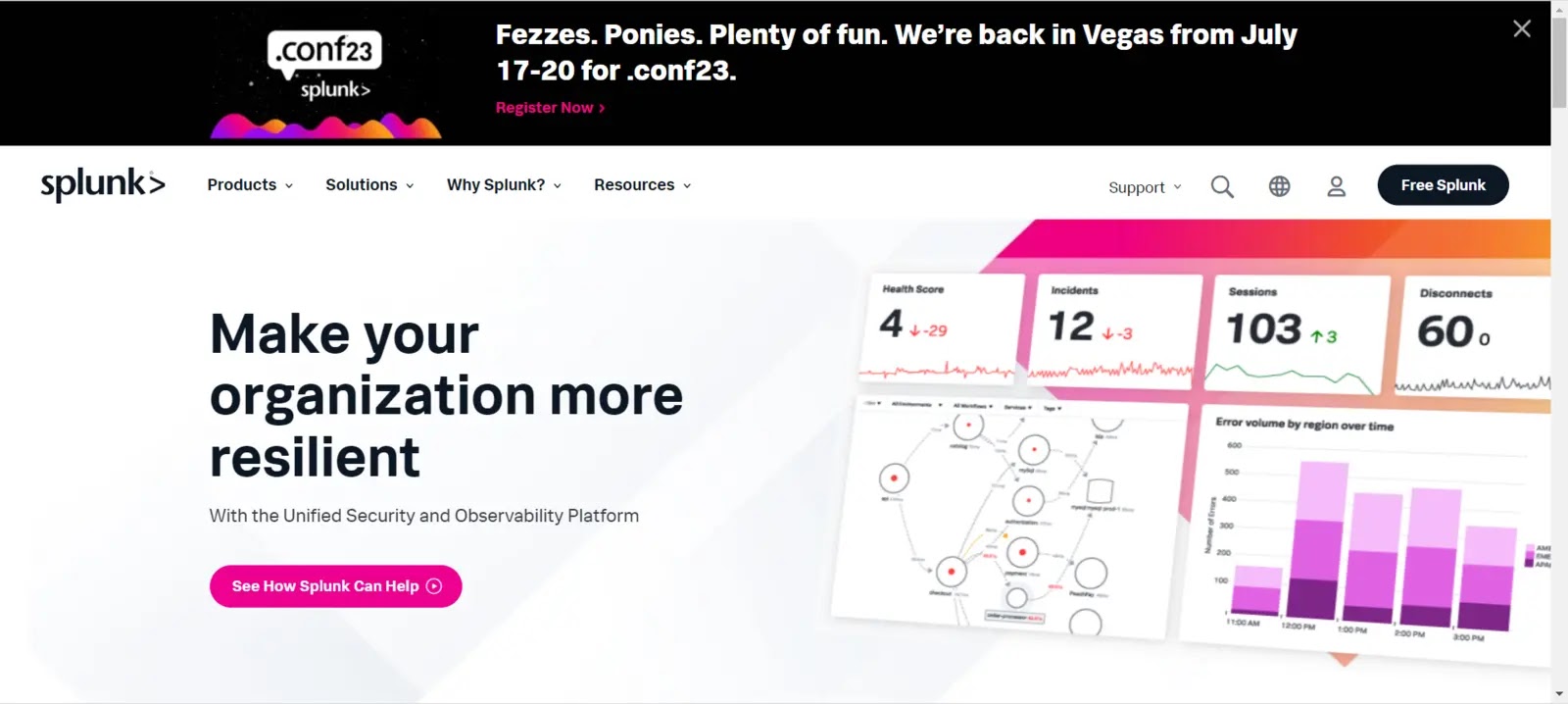
Splunk is one of the most widely used SIEM management software. It separates itself from the market by integrating insights into the core of its SIEM.
Real-time network and device data monitoring is possible as the system searches for potential vulnerabilities and can indicate unusual activity.
The Notables function of Enterprise Security provides notifications that the user can personalize. Splunk Enterprise Security is a highly adaptable solution that includes the Splunk foundation package for data analysis.
You can design your own threat-hunting queries, analysis routines, and automated defensive rules in addition to using the supplied rules. Splunk Enterprise Security is intended for all types of organizations.
However, due to the expense and power of this package, it is likely to be more appealing to large firms than small organizations.
Main Features:
- Real-time security monitoring, alerting, and advanced threat detection using analytics and machine learning for rapid incident identification and response.
- Centralized log collection, correlation, and flexible dashboards for comprehensive visibility across IT, networks, and cloud environments.
- Risk-based alerting and scoring to prioritize threats, reduce alert fatigue, and focus on high-impact incidents.
- Automated investigations, customizable workflows, and integration with threat intelligence for efficient incident management and remediation.
| What is Good ? | What Could Be Better ? |
|---|---|
| Can identify threats not spotted by logs using behavior analysis. | Pricing is unclear; vendor quotes are needed. |
| Nice UI, beautiful, and easy to customize | Fits larger organizations |
| Event prioritization is easy. | |
| Linux/Windows compatible |
3. TrendMicro XDR
.webp.jpeg)
TrenMicro XDR is a security operations center (SOC) tool offered by TrendMicro, a global leader in cybersecurity solutions.
XDR stands for Extended Detection and Response, providing a unified, cross-generational approach to threat protection and security operations.
The tool integrates multiple security technologies, such as endpoint protection, network security, and cloud workload protection, to comprehensively view an organization’s security posture.
XRD automates threat detection and response, streamlines security operations, and helps organizations detect and respond to security threats efficiently.
Main Features:
- Automated correlation of deep activity data across endpoints, servers, cloud workloads, email, and networks for holistic threat visibility.
- Advanced security analytics and machine learning to detect, prioritize, and reduce alerts, delivering higher-confidence incident identification.
- Unified investigation and response workflows enabling faster, more precise incident containment and remediation from a single interface.
- Integration with third-party tools and continuous threat intelligence updates for enriched analytics and optimized security operations.
| What is Good ? | What Could Be Better ? |
|---|---|
| XDR automates numerous manual activities, letting security teams focus on strategy. | It is difficult to manage and configure |
| XDR detects threats using innovative methods. | It is expensive |
| It defends against classic security flaws and new attack vectors. |
4. Trellix Platform
.webp.jpeg)
The Trellix platform enables visibility into network systems in real-time. The instrument enables SOC analysts to view real-time system, network, applications, and database efficiency and activity.
When thoroughly incorporated into a system, analysts are able to study specific occurrences to discover potential problems, such as suspicious activities and poor speeds.
Users of Trellix can additionally add content packs to customize the tool for industry-specific compliance requirements.
Main Features:
- Integrated, AI-powered security platform providing detection, response, and automation across endpoints, email, network, data, and cloud environments for comprehensive threat management.
- Generative and predictive AI enhances threat detection, investigation, and contextualization, enabling rapid analysis and prioritization of alerts and incidents.
- Centralized management with open, extensible architecture and single console for policy, incident response, and seamless integration with third-party tools.
- Automated response and remediation capabilities, including advanced threat intelligence, forensic investigation, and rollback to last known good state for rapid recovery.
| What is Good ? | What Could Be Better ? |
|---|---|
| Accelerate resolution using workflow automation | It doesn’t have the tools that complex websites need. |
| Predict and prioritize assaults | The platform may not be as current or developed as others. |
| Monitor and control all cyber assets from one place. | |
| Integrates with third-party tools and services. |
5. ArcSight
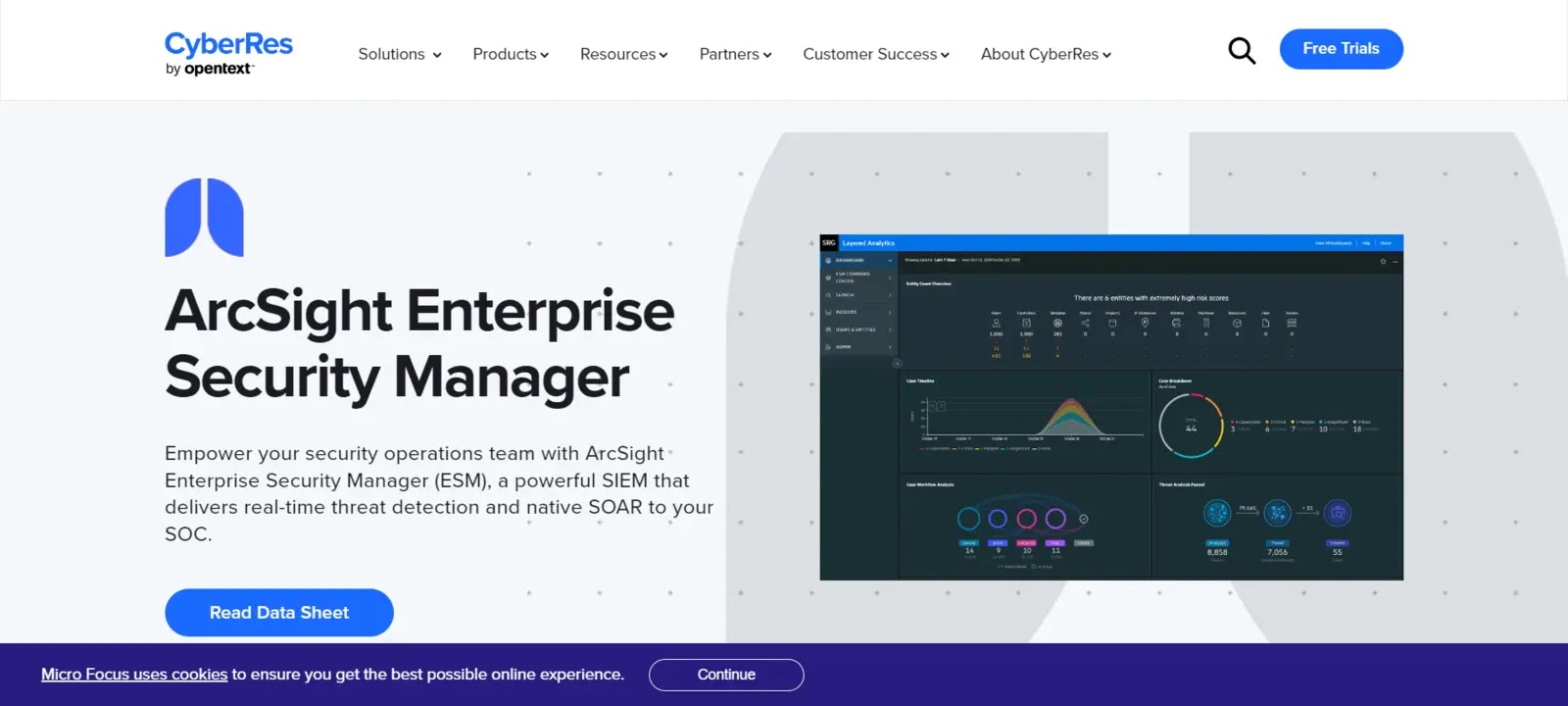
ArcSight is a security information and event management (SIEM) tool offered by Micro Focus, a multinational software company.
The tool provides a comprehensive view of an organization’s security posture, automates threat detection and response, and streamlines security operations.
Main Features:
- Real-time security monitoring, event correlation, and threat detection across diverse sources for proactive threat identification and rapid incident response.
- Advanced analytics, machine learning, and user/entity behavior analytics (UEBA) for detecting anomalies, insider threats, and prioritizing high-risk alerts.
- Comprehensive log management, compliance reporting, and automated workflows for regulatory standards such as PCI DSS, GDPR, and SOX.
- Scalable architecture, big data ingestion, and integration with threat intelligence and third-party tools for centralized security operations and flexible deployment.
| What is Good ? | What Could Be Better ? |
|---|---|
| Integration of threat information on a large scale. | Its numerous security mechanisms make management and configuration challenging. |
| Effective ways to find and deal with incidents. | Small and medium-sized enterprises may find it pricey compared to other security solutions. |
| The ability to handle compliance. | |
ArcSight – Demo/Trial6. Exabeam

Exabeam is a SOC tool offered by Exabeam, a security information and event management (SIEM) solutions provider.
The SOC tool provides a comprehensive view of an organization’s security posture, automates threat detection and response, and streamlines security operations.
Main Features:
- AI-driven threat detection, investigation, and response (TDIR) with advanced user and entity behavior analytics (UEBA) for identifying high-risk threats and anomalies.
- Cloud-native platform for rapid, scalable log ingestion, parsing, normalization, and context enrichment with threat intelligence and user-host-IP mapping.
- Automated investigations and workflows, including dynamic risk scoring and playbooks, to streamline incident response and reduce manual effort.
- Open platform supporting multi-vendor integration, Open API Standard (OAS) compatibility, and centralized management for unified security operations across environments.
| What is Good ? | What Could Be Better ? |
|---|---|
| It enhanced threat identification and security incident response. | It is difficult to manage and configure |
| It takes care of many jobs that used to be done by hand. | It is expensive compared to other security tools |
| It helps security teams act quickly when something goes wrong. | |
| Can work with tools and services from other companies. |
7. Rapid7 Insight Platform
Rapid7 is a cybersecurity startup focusing on monitoring, intelligence, and automation-based security enhancement technologies.
Rapid7’s Insight platform is a SIEM and XDR platform that is supplied via the Rapid7 Insight system with the vendor’s advanced threat, orchestration and management, vulnerability assessments, application, and cloud security products, as well as their systems integration.
Customers of InsightIDR who invest in any of the other Insight products can access all capabilities through a single interface.
Main Features:
- Unified cloud-based platform integrating vulnerability management, detection and response, application security, and threat intelligence for comprehensive security coverage.
- Automated threat detection, investigation, and response with embedded threat intelligence and guided remediation workflows to accelerate incident handling.
- Continuous, real-time visibility and risk prioritization across endpoints, networks, cloud, and applications using advanced analytics and live dashboards.
- Seamless automation and orchestration for security and IT processes, supporting extensive API and third-party integrations for flexible deployment and workflow customization.
| What is Good ? | What Could Be Better ? |
|---|---|
| Provides many security and analytics solutions | May have too many features for simple uses. |
| Integration with security tools is seamless. | Some features take plenty of system resources. |
| Easy cloud deployment and scalability. | |
| Access current threat intelligence. |
8. CrowdStrike Falcon
CrowdStrike Falcon is a SOC tool offered by CrowdStrike, a cloud-delivered endpoint protection solutions provider.
The tool provides a comprehensive view of an organization’s security posture, automates threat detection and response, and streamlines security operations.
Main Features:
- Cloud-native, AI-powered endpoint detection and response (EDR) with next-gen antivirus for real-time threat prevention, detection, and automated remediation.
- Single lightweight agent architecture providing unified visibility, rapid deployment, and scalable protection across endpoints, cloud workloads, and hybrid environments.
- Advanced threat intelligence, behavioral analytics, and proactive threat hunting with integrated MITRE ATT&CK mapping and granular endpoint monitoring.
- Automated incident response, vulnerability and exposure management, and seamless integration with third-party tools and cloud-native workflows.
| What is Good ? | What Could Be Better ? |
|---|---|
| Secures the cloud and scales. | Complex configuration and deployment. |
| Allows fast incident response and repair. | All operating systems may not support some functionalities. |
| Combines endpoint detection, response, and protection. | |
| Combines endpoint detection, response, and protection. |
9. Log360
ManageEngine Log360 is a package for on-premises use that comprises agents for several OS platforms and cloud platforms. The agents gather log messages and transmit them to the server’s central entity.
The integration of agents with over 700 applications to harvest information from them. Additionally, they manage Windows Event and Syslog notifications. As log messages come, the log server consolidates them and displays them in a data viewer in the dashboard.
The application also displays log message details, such as the response time. ManageEngine Log360 is a collection of tools from ManageEngine that includes the EventLog Analyzer.
The EventLog Analyzer package includes all of the log management and threat-hunting features, as well as user tracking, monitoring of file integrity, and Active Directory management.
Main Features:
- Centralized real-time log collection, correlation, and analysis from diverse sources including endpoints, cloud, network devices, and applications for comprehensive security monitoring and compliance.
- Automated threat detection, investigation, and response with AI-driven user behavior analytics (UEBA), anomaly detection, and integrated threat intelligence feeds.
- Advanced data and file integrity monitoring, integrated DLP, and sensitive data discovery to prevent data exfiltration and insider threats.
- Automated incident response workflows, compliance reporting, and regulatory templates for standards such as PCI DSS, HIPAA, SOX, and ISO 27001.
| What is Good ? | What Could Be Better ? |
|---|---|
| File integrity surveillance | Initial setup and configuration can be complex. |
| Manual data analysis tools | May require significant hardware resources. |
| Automated threat detection | |
| Compliance management and log management |
10. McAfee ESM (Enterprise Security Manager)
In terms of analytics, McAfee Enterprise Security Manager is recognized as one of the top SOC tools. Through the Active Directory system, the user can collect a variety of logs from a large number of devices.
McAfee is a strong and trustworthy brand; therefore, when it offers an appropriate security solution, you must pay close attention. McAfee’s correlation engine integrates various data sources with relative simplicity in terms of simplification.
This significantly simplifies the detection of security events. Users have access to both McAfee Enterprise Technical Support and McAfee Business Technical Support in terms of support.
The user has the option of having a Support Account Manager visit their site twice per year. The McAfee platform is designed for mid-to-large enterprises seeking a comprehensive safety event management platform.
Main Features:
- Real-time event correlation and advanced analytics for proactive threat detection, investigation, and rapid incident response across diverse data sources.
- Comprehensive log management with scalable, centralized collection, storage, and long-term retention for forensic analysis and compliance reporting.
- Integration with threat intelligence feeds and customizable dashboards for enriched context, prioritized alerts, and streamlined security operations.
- Robust compliance support and workflow automation with built-in templates, case management, and policy enforcement for regulatory adherence and efficient incident handling.
| What is Good ? | What Could Be Better ? |
|---|---|
| Uses a powerful correlation engine to identify and reduce hazards faster. | More integration options would be beneficial. |
| Highly compatible with Active Directory environments | The interface is frequently crowded and overwhelming |
| Designed with massive networks in mind | |
| Aids regulatory compliance. |



